No… You are but one worker. The CEO has a hundred of you under him. All 100 of you are pushing the button.
That would be 200x of what you make. Which is basically correct.
Nope. I don’t talk about myself like that.
No… You are but one worker. The CEO has a hundred of you under him. All 100 of you are pushing the button.
That would be 200x of what you make. Which is basically correct.


The fact that I addressed some of these items literally line by line and you bring it up again as if I didn’t address it tells me that you’re arguing in bad faith. Have a good day. Find someone else to complain to.


Forgive me for not covering 100% of this advanced topic in my 3 paragraphs on Lemmy… Nuance gets long, and most people have attention spans of a squirrel.
maybe it’s hard to distinguish between google services, but if you play some online game, chat over whatsapp or signal, or have a voip call, that’s an entirely different story.
Already covered as
That leaves just the raw connection analysis…
Where specifics can’t be divined… but other details might.
these can probably be told apart by DNS requests
Addressed already with
DNS by default is often plaintext. You can setup your device to use DoH or other encrypted versions of DNS.
when having a voip call, through a service that supports peer to peer calls (most do, and it’s default on), an observer may even be able to deduct something about who you are speaking with, like what general area they live at.
Actually this is quite unlikely. ASNs are not as structured as you think. It takes an external database that specifically tracks DHCP’d ISP addresses. Case in point, when I moved to my new house… Google maps though I was a good 60 miles away from where I was… it was after repeated access to google maps and other service for about a month before maps started getting accurate with where I’m accessing their service from.
And that point is covered with
It would take a bunch of external additional data to actually tie you to anything directly, eg server logs or other sources… which usually means more than one party is already working together against you. At that point you’ve got bigger issues usually.
then what if you have apps that try to establish connections to services at home.
If you purposefully steer your car off the road… of course you’re going to crash. If you’re going to expose non-encrypted things onto the internet…
At that point you’ve got bigger issues usually.
I would suspect the untrusted wifi to NOT be the leading thing you’d want to care about in this situation. But even then… I would start making reasonable assumptions such as you’re likely on a DHCP connection without static addressing… your site and resources will rotate IPs every once in a while. Makes tracking you even harder.
with HTTPS you leak your internal domain names because of TLS SNI.
Encrypted SNI (ESNI) / Encrypted Client Hello (ECH) exists… Cloudflare for example supports ECH, and they transit a LOT of data.
But once again… would be outside of the scope of discussion here. Yes… an ISP can make an educated guess of where you’re likely to be going… and maybe even make a reasonable guess of what you could doing… But certainly not the details of it.
And this all ignores the fact that a random coffee shop isn’t going to do full packet inspection to get this data to begin with. It’s not worth it for them. They gain very little from collecting meta data without some bigger company backing them to do so… Which falls under
It would take a bunch of external additional data to actually tie you to anything directly, eg server logs or other sources… which usually means more than one party is already working together against you. At that point you’ve got bigger issues usually.
Edit: Typo that changed meaning. Fixed.


The X is for the syncing phone book notification… It’s not on the notice itself.


HTTPS is used on virtually every site out there these days. That is used to encrypt your traffic from the get go. So specifics of the traffic/request won’t be obvious/known. The EU could be big enough to force manufacturers to inject their certificates into devices… could be a man in the middle attack. But you can always just remove certs you don’t trust from your devices.
DNS by default is often plaintext. You can setup your device to use DoH or other encrypted versions of DNS.
That leaves just the raw connection analysis… eg, that your device is sending traffic to some known IP… many site share hosts so that can be hard to determine though often not really… Proxy or VPN services can make it impossible to do this type of analysis… but then those services will be able to tell.
Ultimately being able to say that “Shalafi sent some packets to an IP that google owns and received a bunch back” could be email… could be youtube… could be any number of things… at some point it become educated guess at best. And what specifically happened (ex: Watched a video about tying shoes) is simply unknown. It would take a bunch of external additional data to actually tie you to anything directly, eg server logs or other sources… which usually means more than one party is already working together against you. At that point you’ve got bigger issues usually.
Open all of them… Only place cover back when you’re done.
Adding a member to a vdev does not automatically move any of the parity or data distribution off the old vdev.
Yes it does. ZFS does a full resilver after the addition. Jim Salter’s write ups are from 4 years ago. Shit changes.
Edit: and even if it didn’t… It’s trivial to write a script that rewrites all the data to move it into the new structure. To say there’s no valid cases when even in 2021 there was an answer to the problem is a bit crazy.


Illinois Governor isn’t going to be doing anything… The warrant is only valid within Texas. They’re not going to come to Illinois to kidnap them.


I’m literally looking at my DNS records at cloudflare
PTR records are NOT on the domain side.
https://www.cloudflare.com/learning/dns/dns-records/dns-ptr-record/
An example record lookup would be 8.8.8.8.in-addr.arpa. Like I’ve said twice now. YOU don’t control google’s PTRs (since you linked to google workspaces). They DO have PTRs setups.
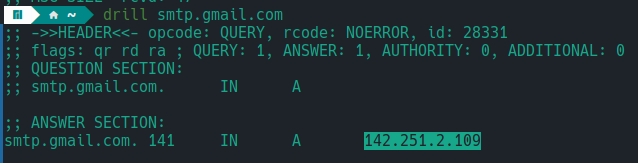
IP of 142.251.2.109 resolved for my DNS.
https://easydmarc.com/tools/ptr-record-lookup?domain=142.251.2.109&dns_server=1.1.1.1&dns_type=PTR
Resolves to a record name of dl-in-f109.1e100.net
Edit: Another name for a PTR record is rDNS. Or Reverse DNS. and that name is a bit more descriptive in that it’s IP -> Name rather than DNSes normal job of Name -> IP address


Your page is explicitly a support page for dkim config. It is not a list of email requirements. YOU don’t control their ptr records. Ptr records are placed on the IP space side. Google controls theirs for workspaces. So that page won’t have help on the matter. Requirements haven’t changed. I control systems that send millions of messages a month…
Ptr, SPF and dkim are now mandated. Dmarc is highly recommended for gmail…
Edit:
https://forum.directadmin.com/threads/gmail-rejecting-emails-due-to-missing-or-incorrect-ptr-record-–-how-to-set-this-up-correctly.72802/
https://www.reddit.com/r/webdev/comments/1foik1l/false_error_message_does_not_have_a_ptr_record/
https://dmarcreport.com/blog/googles-guidelines-to-send-emails-to-gmail-users/
How many links you need before you recognize that you’re wrong? All three of these are from last 10 months. One of which was from March.


The first link in my previous comment is literally gmail returning an error because no ptr…
Edit: your page is about setting up dkim while using their workspaces. You don’t control their ptrs.
Edit2: notice they don’t talk about SPF or dmarc on that page either. SPF has been require for google as well for a while and dmarc is highly recommended though not strictly required.


https://www.reddit.com/r/sysadmin/comments/1iu0x33/anyone_else_seeing_ptr_record_issues_with_m365/
Yes you do need a ptr. The big services will outright block you.


But getting a static address for your VPS is likely much easier than getting it from certain ISPs.
For instance, Quantum Fiber doesn’t support static IPs at all… But most VPSes can and do.


ISP’s NAT
That has it’s own name… CG-NAT. Thus why people are responding to you as if you’re wrong. As you wrote it you are wrong though. But there’s still answers like argo tunnels (if you are okay with cloudflare) and other similar solutions.
Or you can setup a vps and tunnel through that.


Your local college might do networking courses/stuff. honestly though, there’s enough youtube content out there by really respected people that you can likely just get away with that… Start with words/topics you see mentioned in this thread. Example, search youtube for DDNS… and if that video says something you don’t understand search for that topic. Eventually you’ll have a decent grasp on what’s going on.


Then you have a SIP trunk provider that doesn’t validate domain ownership… I’d like to know that companies name if you don’t mind sharing. They’re stupidly rare to the point that I view it as a unicorn situation.
Edit: To clarify, I’ve tried finding such providers and failed for several years… They all want PTR validation for “security”


PTR lookups has been a thing for email servers for a very long time… “used to work fine” would have been early 2000’s as far as I can remember.
PTR is de facto requirement for over 20 years now. So unless you’re talking about pre-turn of the century, not really… email servers haven’t worked without PTRs for a very long time.
I had to look it up, but Yahoo and AOL implemented PTR checks in 2003-2004. Gmail had it out of the box in 2004.
Can you run a server without it? Yes… and it will work with any other server that doesn’t mandate valid PTR records. But no major consumer email server has supported receiving mail from a PTR-less server for 20+ years now. So you’re not going to be able to email basically anyone from your server.


Well yes… but if you’re goal to self-host is to control your data, it’s a bit counter productive to use those relays services that inject that problem right back into your setup again.
Edit: I’m not necessarily arguing… just putting the information out there that the services exist, but might not be a good fit.


Yeah that’s another option as well… Services like dynu.com or smtp2go.com do exist… but you have to pay for them and there is a risk that the service can open/read your messages.
“imagine making 50% of what the CEO makes” - Means the CEO makes a mere 2x…
2 * 100 = 200. Pretty sure I did the math right.
At 50k a year, 50k * 200 is 10 million for the CEO.
Which is page 46 of this CEO pay list. https://aflcio.org/paywatch/highest-paid-ceos?page=46
Pretty sure my throw away statement that I literally did no work to actually fact check actually happens to be quite accurate.